Keysight Delivers New IoT Security Assessment Test Software
Offers comprehensive and automated cybersecurity validation of IoT devices
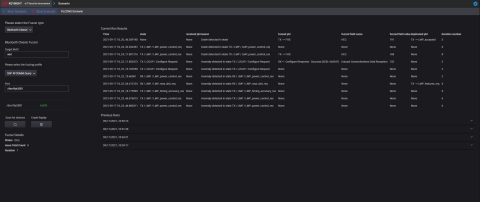
Keysight’s IoT Security Assessment software shows test results with zero day findings in Bluetooth. (Graphic: Business Wire)
Increasing numbers of connected IoT devices enable hackers to leverage cybersecurity vulnerabilities for a range of attacks including malware, ransomware and exfiltration of data. According to Statista, the total installed base of IoT connected devices worldwide is projected to grow to 30.9 billion units by 2025 from 13.8 billion units expected in 2021.
“IoT device vulnerabilities are especially dangerous as they can facilitate sensitive data breaches and lead to physical danger, such as industrial equipment malfunction, medical device defects, or a home security system breach,” wrote Merritt Maxim, vice president, research director, and
IoT Security Vulnerabilities – BrakTooth Discovery
Recently, researchers at
BrakTooth captures fundamental attack vectors against devices using Bluetooth Classic Basic Rate/Enhanced Data Rate (BR/EDR) and is likely to affect Bluetooth chipsets beyond those tested by the SUTD team. "It is hard to accurately gauge the scope of BrakTooth affected chipsets,” commented
The vulnerabilities, which include 20 common vulnerabilities and exposures (CVEs), as well as four awaiting CVE assignments, are found in Bluetooth communication chipsets used in System-on-Chip (SoC) boards. These pose risks that include remote code execution, crashes and deadlocks. The SUTD team responsibly disclosed the findings to the affected vendors, providing a means to reproduce the findings and time to remediate vulnerabilities.
“Research activities like these at SUTD are critical to improving cybersecurity in the connected world. If the good guys don’t improve it, the cyber criminals will take advantage of vulnerabilities for nefarious purposes,” said
Keysight’s
Keysight’s IoT Security Assessment software leverages more than 20 years of experience in network security testing to reveal security vulnerabilities across any network technology. The software offers comprehensive, automated testing to rapidly cover a large matrix of known and unknown vulnerabilities. IoT security assessments include novel cybersecurity attack tools and techniques for wireless interfaces such as Wi-Fi, Bluetooth, and Bluetooth Low Energy (BLE) to test known vulnerabilities, as well as to discover new vulnerabilities.
Development organizations can easily integrate Keysight’s API-driven solution into their development pipeline with a single API for control and reporting. Organizations deploying IoT devices can leverage the software to validate IoT devices before they are delivered to end users and as new vulnerabilities become a concern. Ongoing research from Keysight’s
About
Keysight delivers advanced design and validation solutions that help accelerate innovation to connect and secure the world. Keysight’s dedication to speed and precision extends to software-driven insights and analytics that bring tomorrow’s technology products to market faster across the development lifecycle, in design simulation, prototype validation, automated software testing, manufacturing analysis, and network performance optimization and visibility in enterprise, service provider and cloud environments. Our customers span the worldwide communications and industrial ecosystems, aerospace and defense, automotive, energy, semiconductor and general electronics markets. Keysight generated revenues of
Additional information about
_______________
1 Forrester, The State of IoT Security, 2021, by Merritt Maxim,
View source version on businesswire.com: https://www.businesswire.com/news/home/20211013005753/en/
+1 609-994-7442
beth.hespe@keysight.com
+81 42 660-2162
fusako_dohi@keysight.com
Source:









